Security measures
Password Policy
Please refer to password policy
Multi-factor authentication
TOTP (Time-based One-time Password) based two-factor authentication can be configured for FutureVuls login. You can also check whether or not a user has multi-factor authentication from the administration screen.
Notify users of unauthorized logins and take action
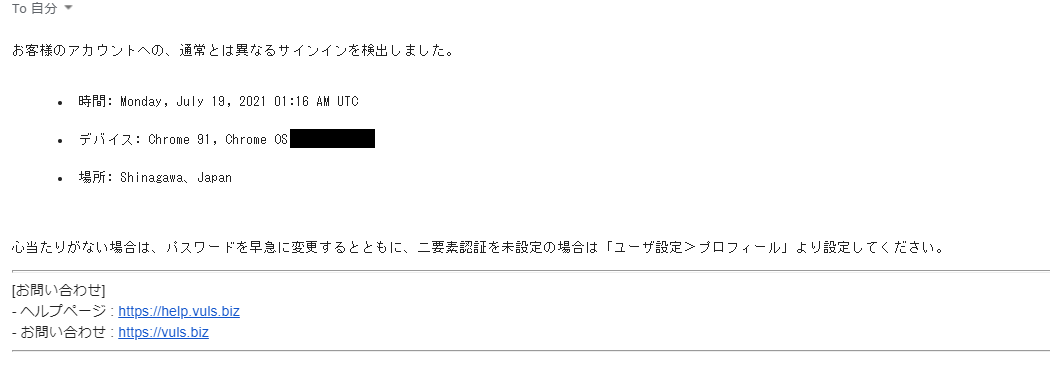
Notification is sent to the registered e-mail address when an unusual login is detected.
If you do not recognize the login information listed, there is a possibility that your password has been compromised by a third party.
Please change your password or set up two-factor authentication.
This feature is available in Amazon Cognito advanced security.
It is assumed that users will learn about their environment by using the portal, but if they don’t, please contact us at Contact Us.
Disable users with invalid email addresses
Access to the portal screen will be restricted for users who no longer receive emails from FutureVuls.
For example, you can prevent unintended users from continuing to use your service due to forgotten to remove a user who left the company from the group.
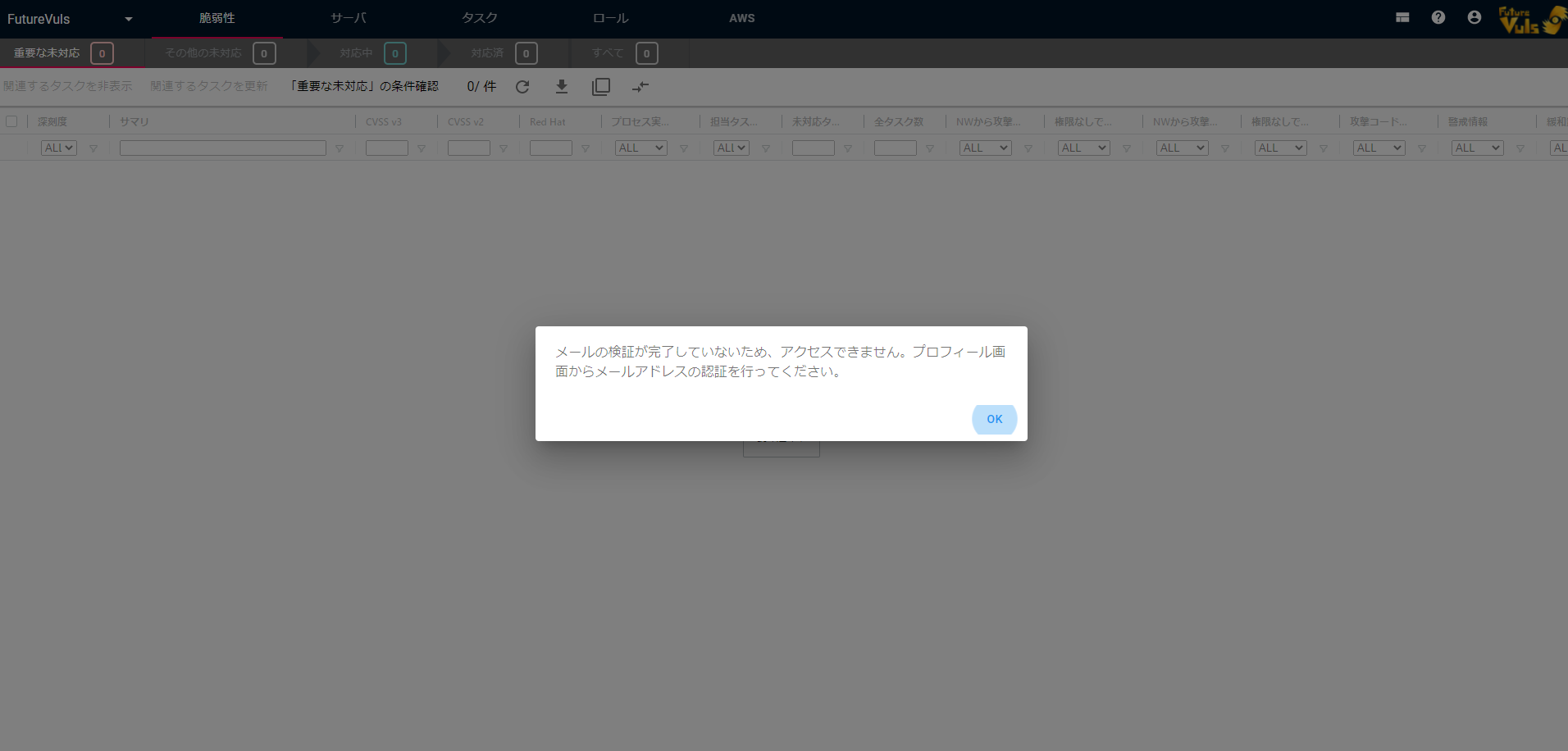
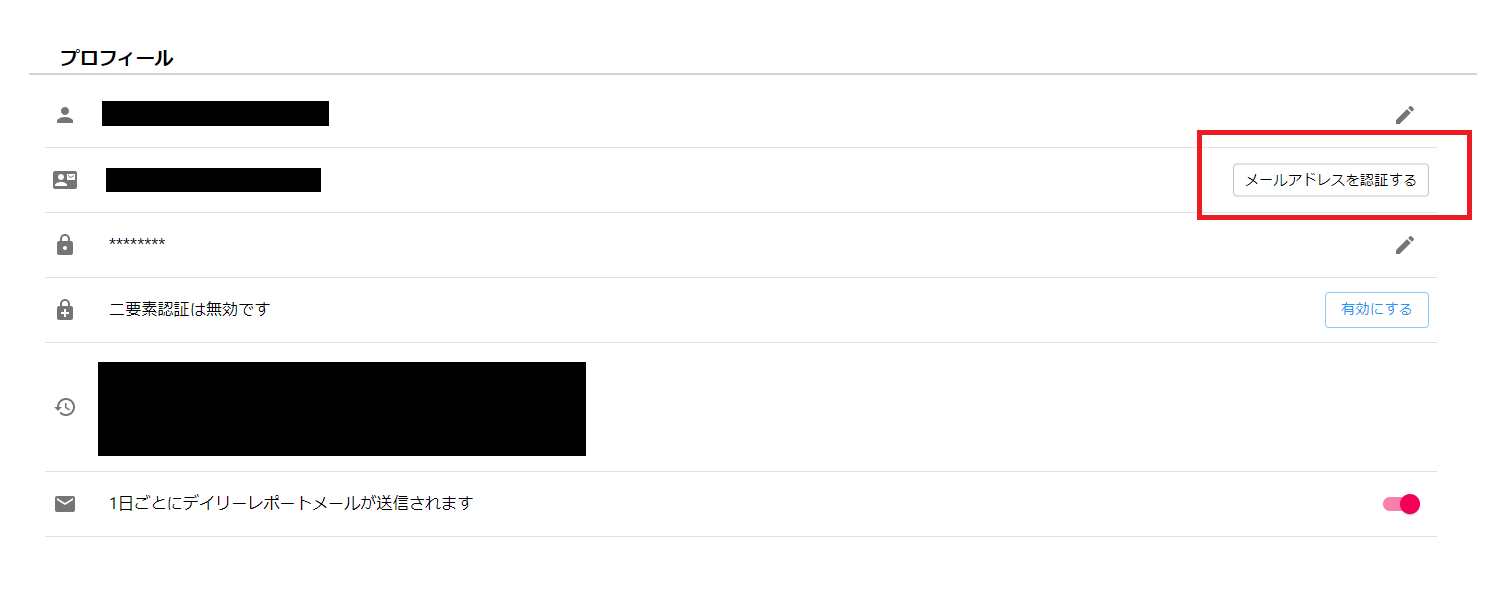
When an email sent by FutureVuls goes into bounce status, the restriction will be applied and only the profile screen will be available for viewing. If you wish to reactivate an account that has been deactivated, please make sure that your registered address is still valid, log in, and re-authenticate from your profile page. An activation code will be sent to your email address. Your FutureVuls account can only be restored if you are able to receive the verification code by email.
IP address restriction
You can restrict IP addresses that can access FutureVuls by specifying IP address.
Security authentication
Please refer to the following https://www.future.co.jp/architect/privacy_policy/
Will data be sent to foreign countries?
As of January 2020, no data will be sent outside of Japan.
Cloud service operational aspects
- We have enabled the security features of AWS’s Authentication Information Managed Services.
- AWS threat detection mechanisms are in place.
- Source code static analysis type security checks are built into CI.
- We conduct vulnerability assessments on a regular basis.
Protection of information uploaded to cloud services
- Uploaded information is encrypted (both in route and storage)
- Temporary key with expiration date is obtained at the time of uploading, instead of using a permanent access key.
- Access privileges to upload destinations are controlled by organization/group.
- Only uploading is allowed. (There is no global access permission to the upload destination.)
Password list attack prevention
Account is locked for a certain period of time when the number of password attempts exceeds a certain number.
Audit log
CSIRT plan allows you to view and CSV download the operation history of users belonging to the organization.